We’re upgrading your documentation experience!
A new doc website is live at docs.openit.cloud — a temporary preview during our transition. This website is now in maintenance-only mode (only critical issues will be addressed).
Explore the new website and send us your feedback!
#
Access Management
You must be an Administrator to manage local users, their roles, and access controls.
#
Managing Roles
#
Roles and Permissions
CLIMS has two (2) pre-made roles:
This is the built-in admin role that has full access permission. Administrators have the full capabilities to manage CLIMS Server and the license servers connected to it. They are also the only users that can navigate to the Identity Server interface and Administration tab to grant privileges to identity roles and users.
The default admin account created upon CLIMS Server installation has the Administrator role.
The user who installed the CLIMS Server automatically becomes an Administrator.
See the list of administrators in Authentication.json in C:\Program Files\OpeniT\Zero\Configuration by default.
This role has limited access permission, specifically for license server monitoring only.
The table below shows the capabilities available for each role/permission.
By default, all members of the Active Directory have the user role, which has limited access permission.
#
Add a New Identity Role
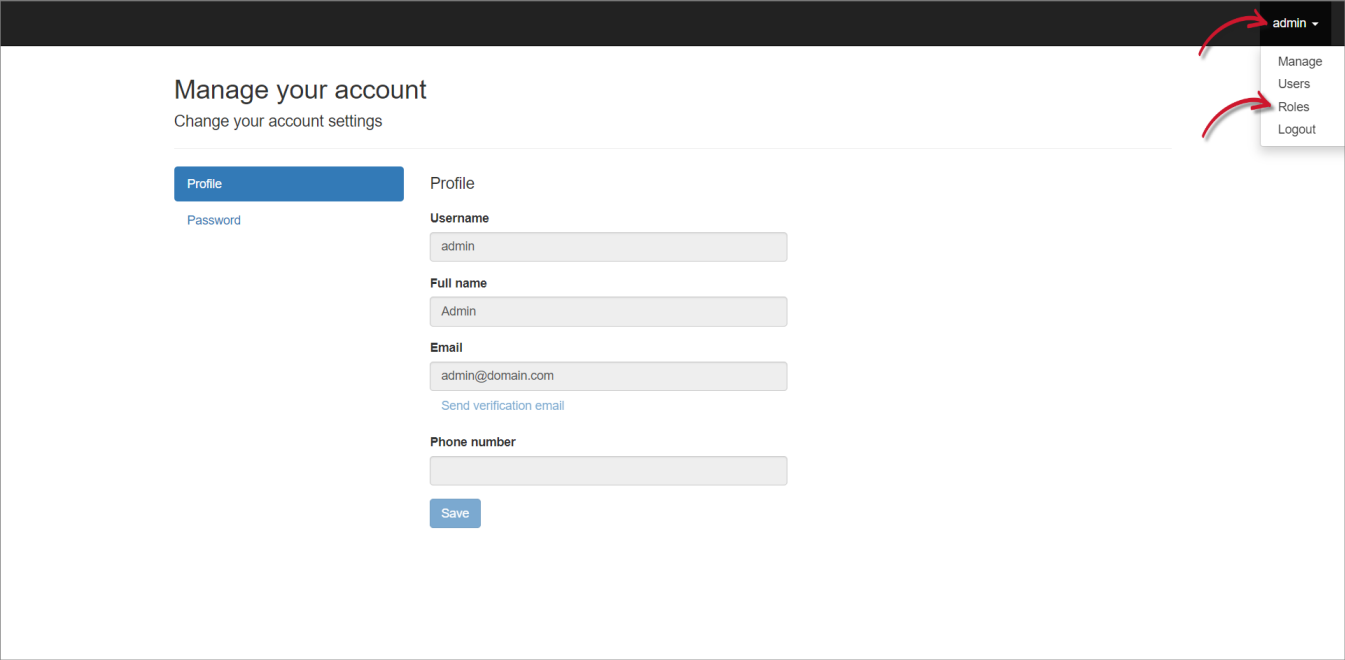
Log in using an Administrator account.
On the upper-right corner of the page, click on the username, then select Manage.
- Once redirected to the Identity Server interface, click on the username again, then select Roles.
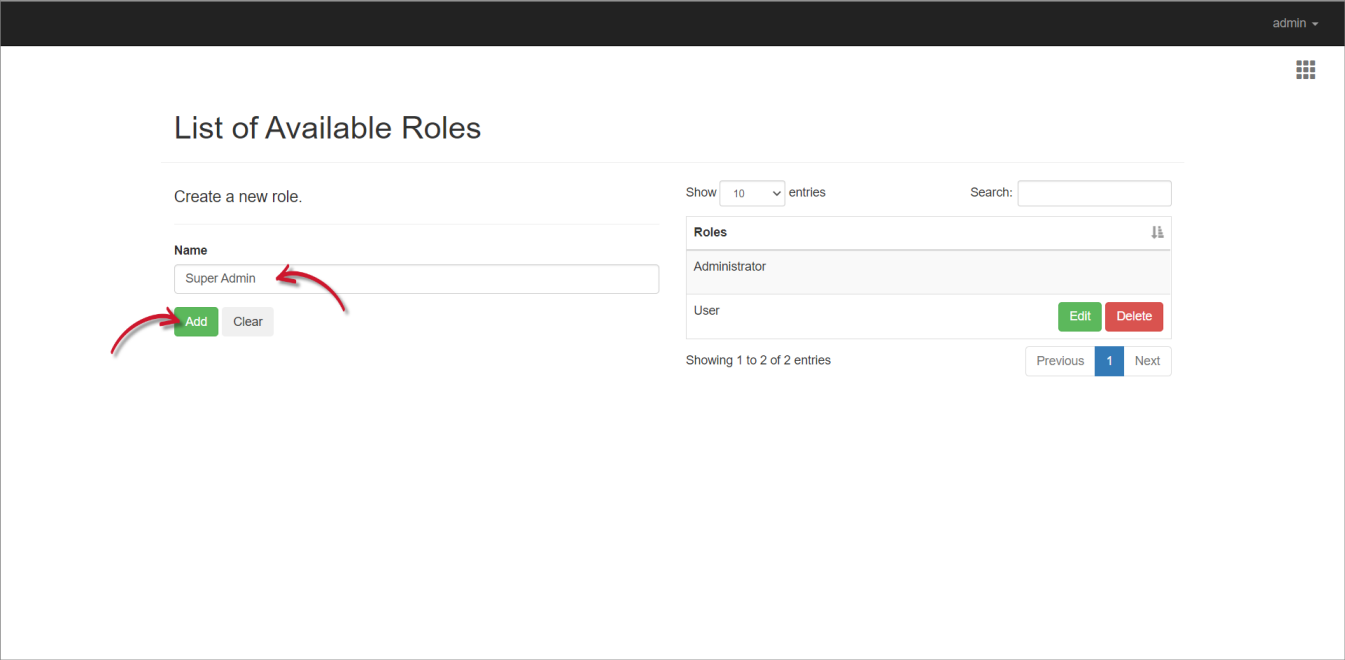
- Under Create a new role, type in the Name of the new role, then click Add.
#
Edit an Identity Role
Log in using an Administrator account.
On the upper-right corner of the page, click on the username, then select Manage.
- Once redirected to the Identity Server interface, click on the username again, then select Roles.

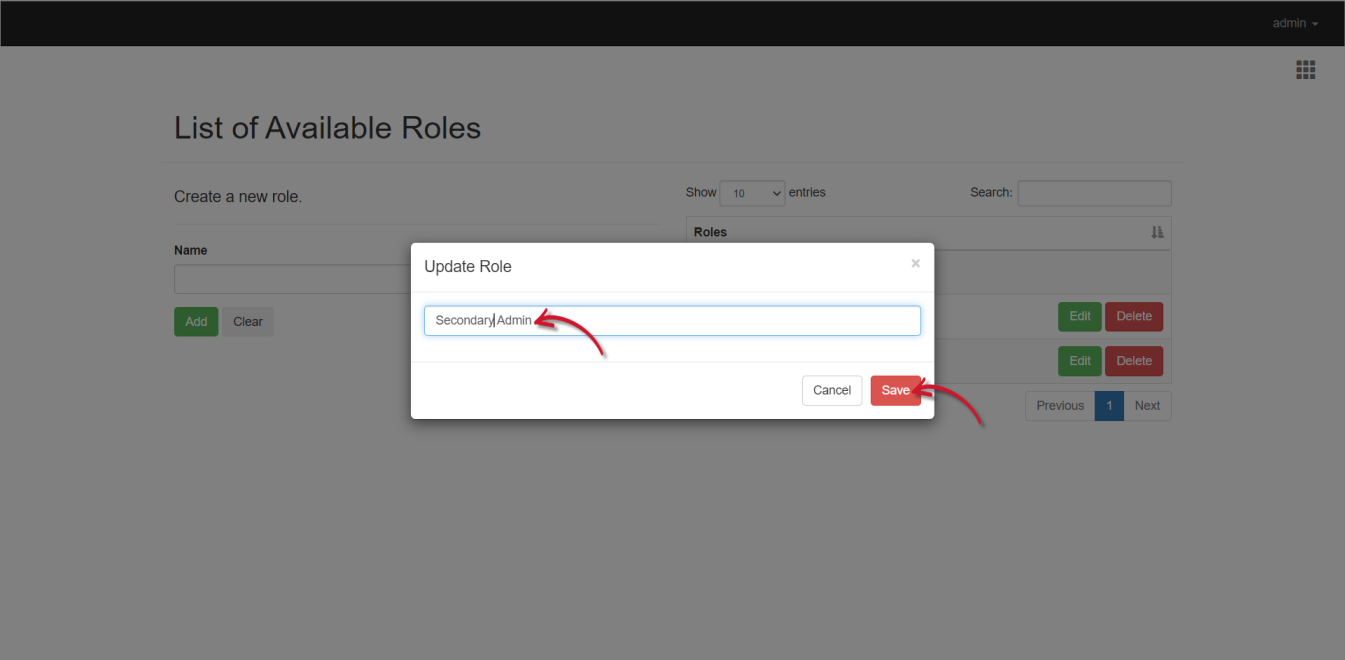
- Click the Edit button of the target role.
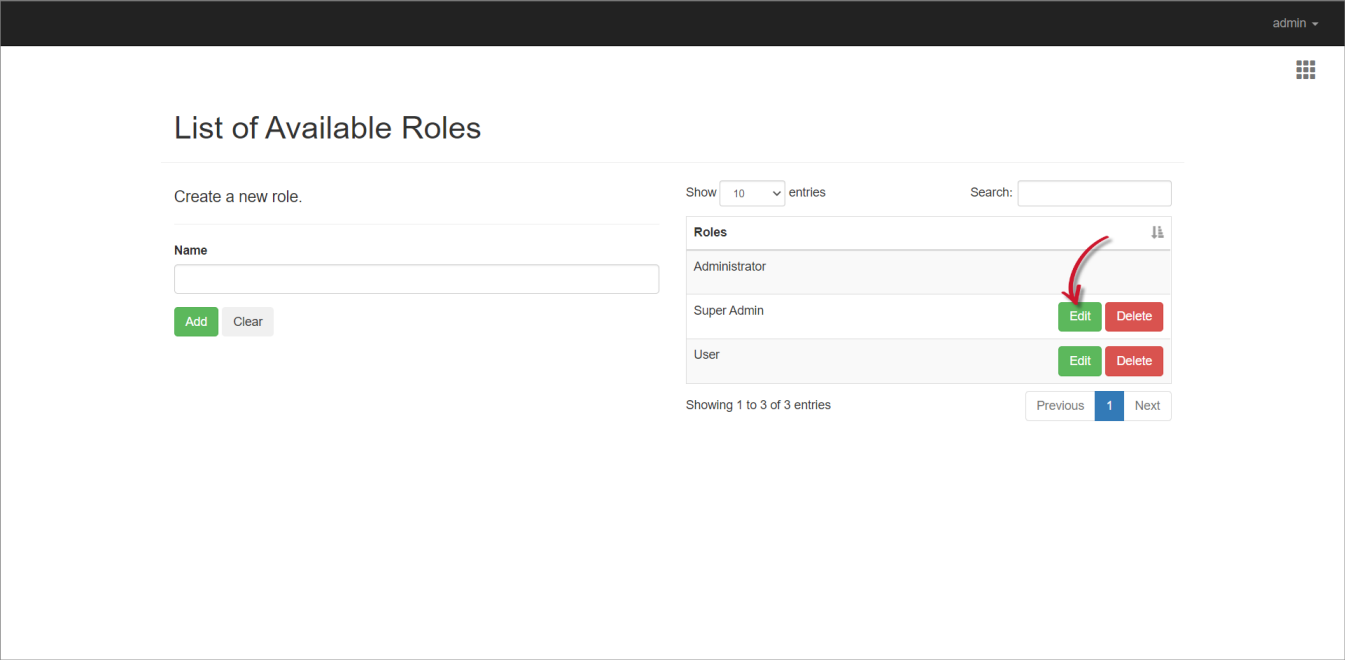
Modify the role information.
Click Save.
#
Delete an Identity Role
Log in using an Administrator account.
On the upper-right corner of the page, click on the username, then select Manage.
- Once redirected to the Identity Server interface, click on the username again, then select Roles.

- Click the Delete button of the target role.
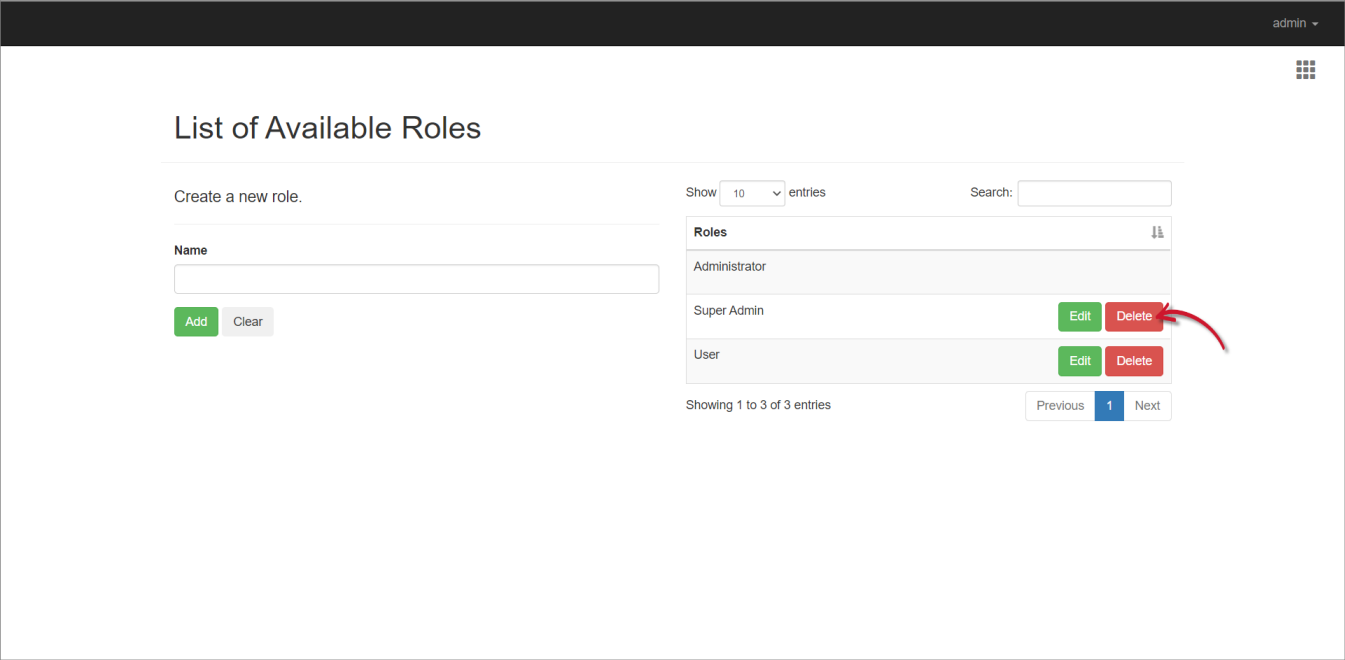
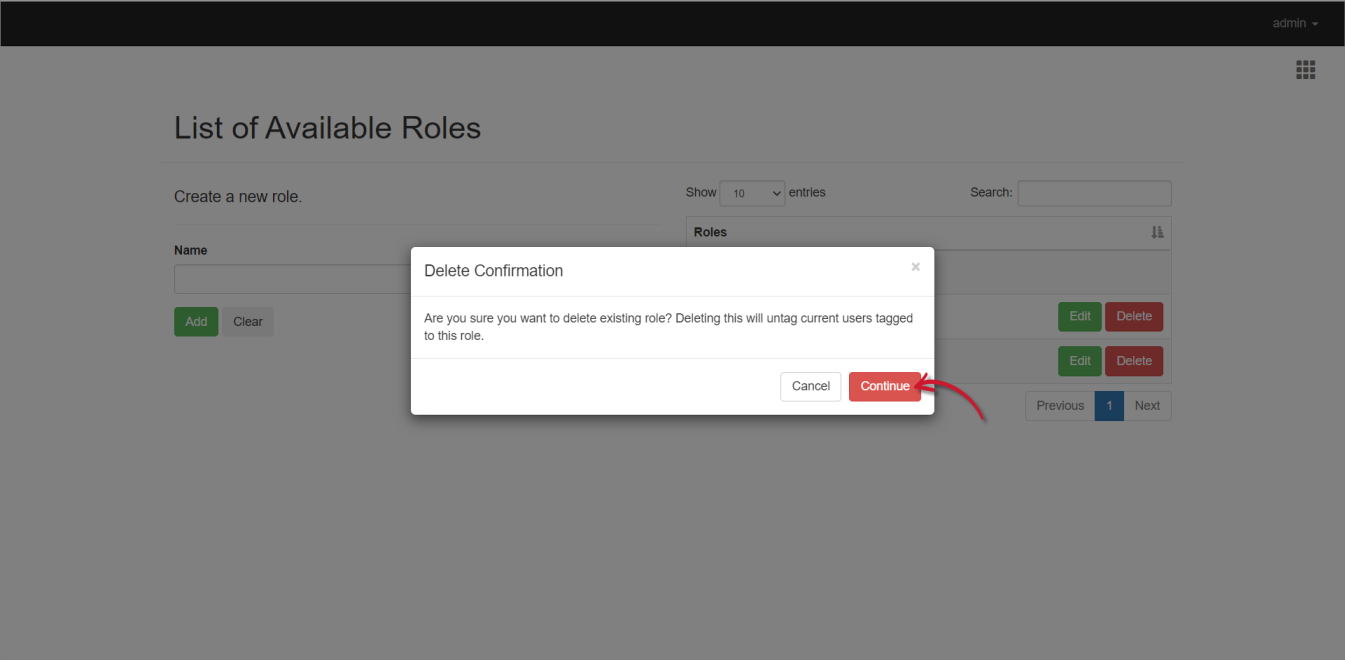
- Click Continue to proceed.
#
Add a Domain User or Group to the Administrator Group
To do this, you need to access the machine where the CLIMS Server is installed.
Go to the Configuration folder, which is
C:\Program Files\OpeniT\Zero\Configurationby default.Create a copy of
Authentication.jsonand rename the duplicate file toAuthentication.Override.json.Open the existing
Authentication.Override.json, if there is already one.In the override file, add the new user(s) and/or group(s) under Administrators following the
domain\\nameformat.
...
24 | },
25 | "Administrators": [
26 | "DOMAIN\\user1",
27 | "SVG\\johnsmith",
28 | "SVG\\development-grp"
29 | ]
...
#
Managing Local Users
#
Add a New Local User
Log in using an Administrator account.
On the upper-right corner of the page, click on the username, then select Manage.
- Once redirected to the Identity Server interface, click on the username again, then select Users.
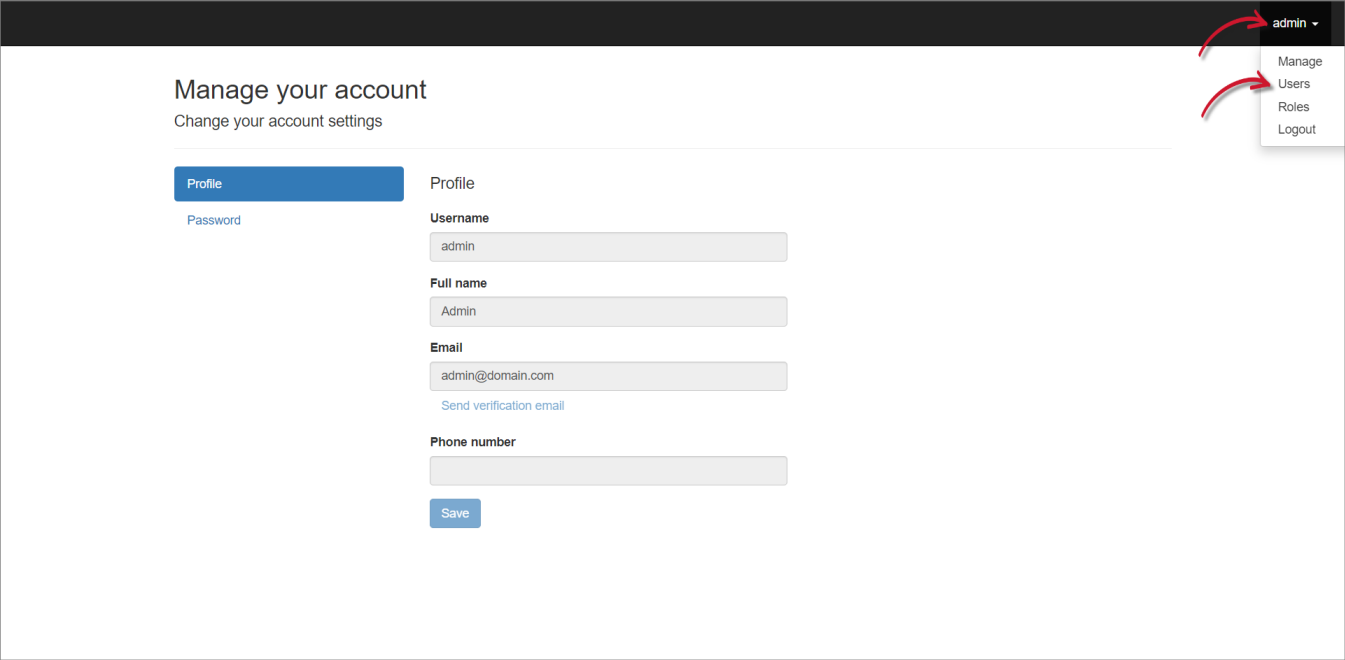
- Click Register new user.
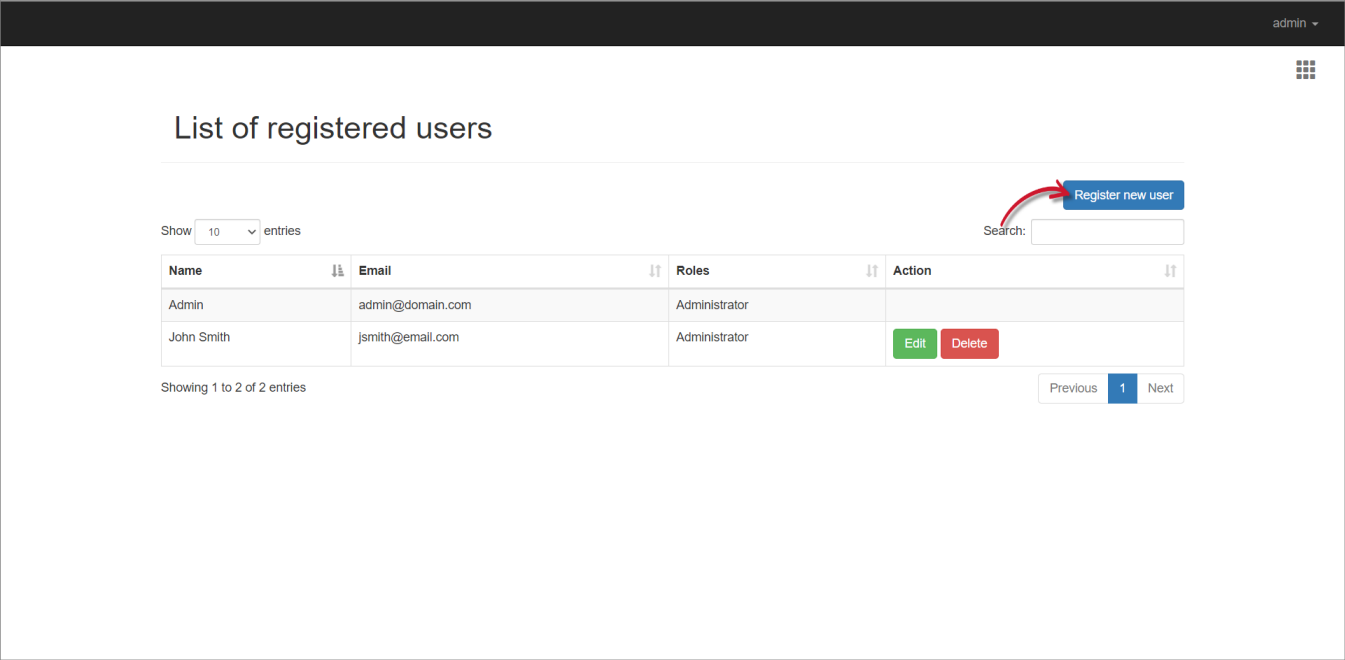
Provide the needed details in the registration form.
Click Register.
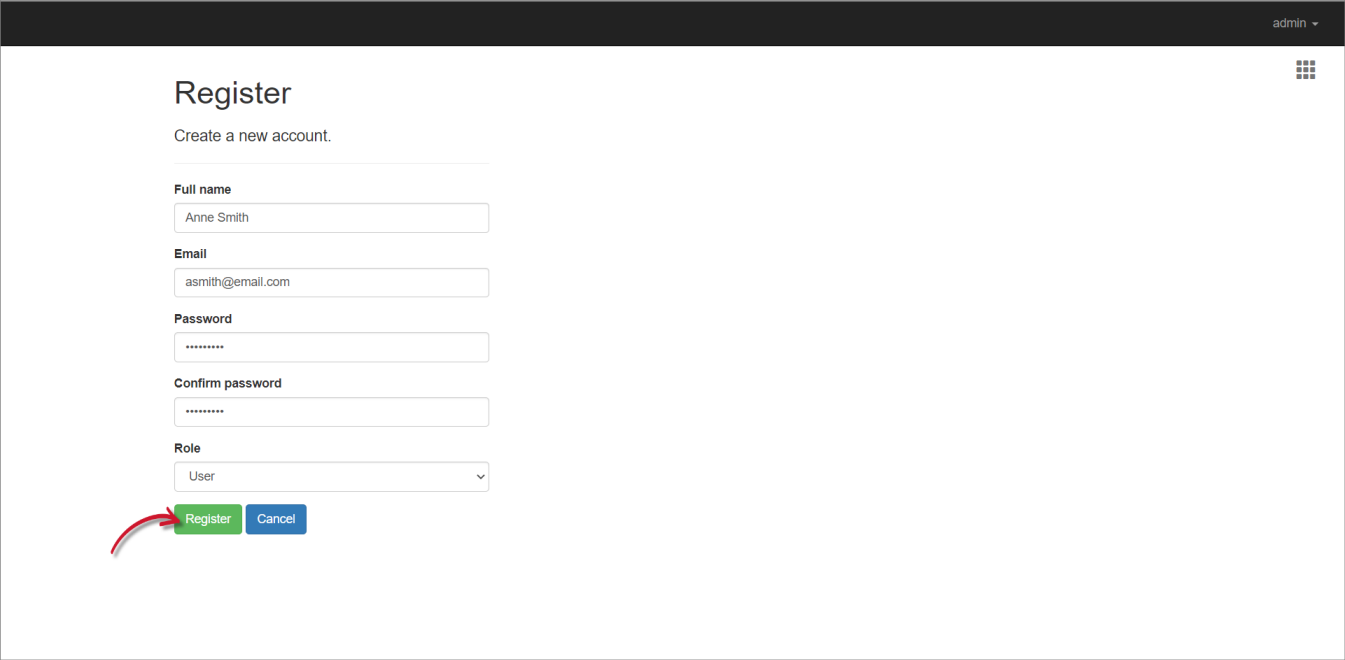
The password must have at least one non-alphanumeric character, one lowercase, and one uppercase letter.
#
Edit Local User Details
Log in using an Administrator account.
On the upper-right corner of the page, click on the username, then select Manage.
- Once redirected to the Identity Server interface, click on the username again, then select Users.

- Click the Edit button of the target user.
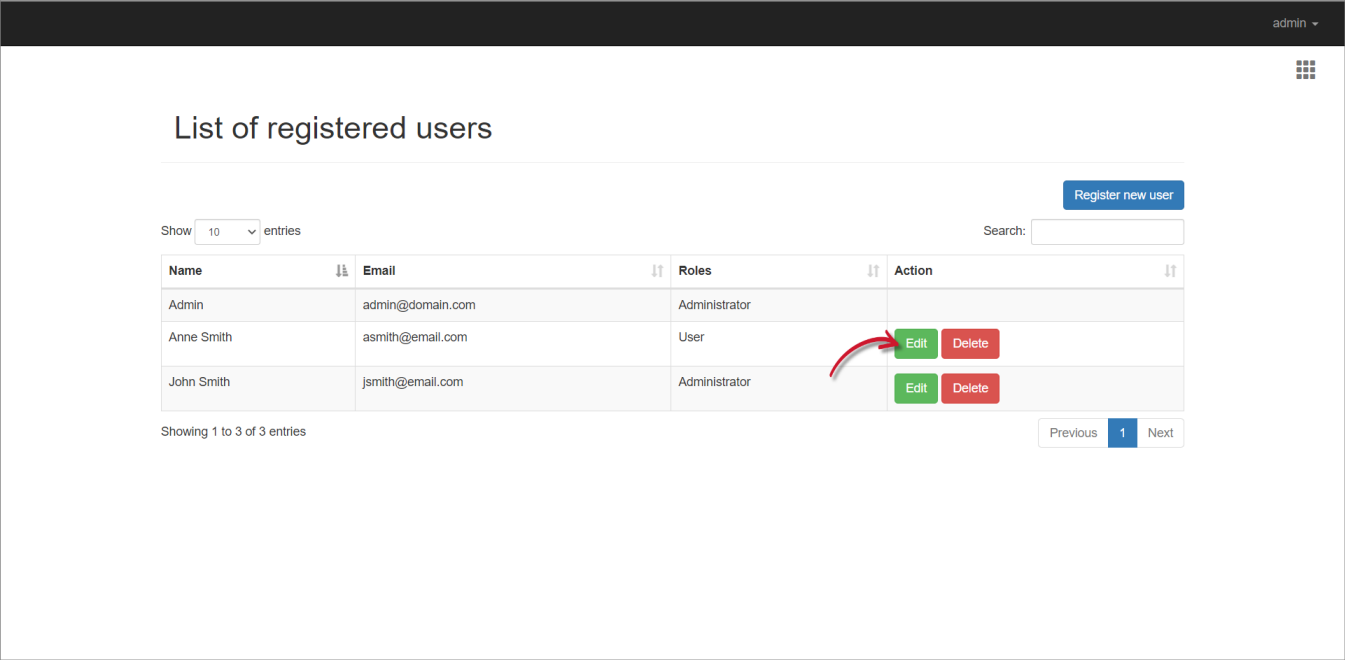
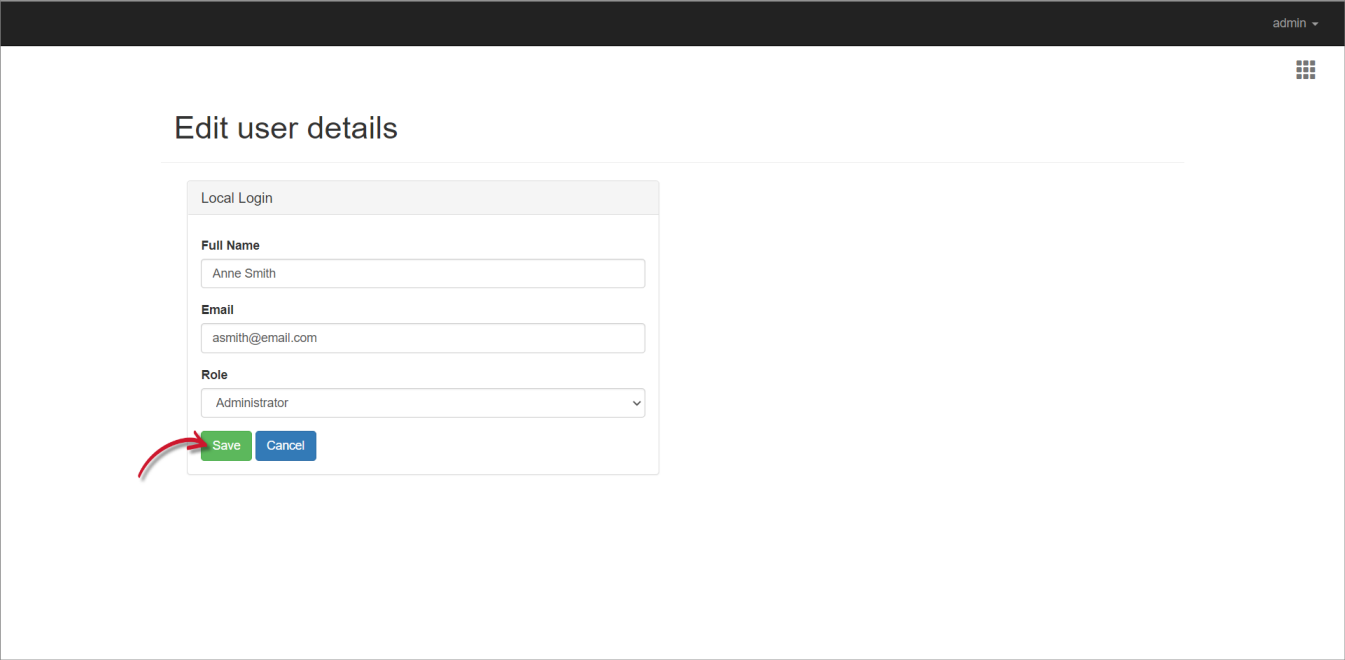
Update the details as needed.
Click Save.
#
Delete a Local User
Log in using an Administrator account.
On the upper-right corner of the page, click on the username, then select Manage.
- Once redirected to the Identity Server interface, click on the username again, then select Users.

- Click the Delete button of the target user.
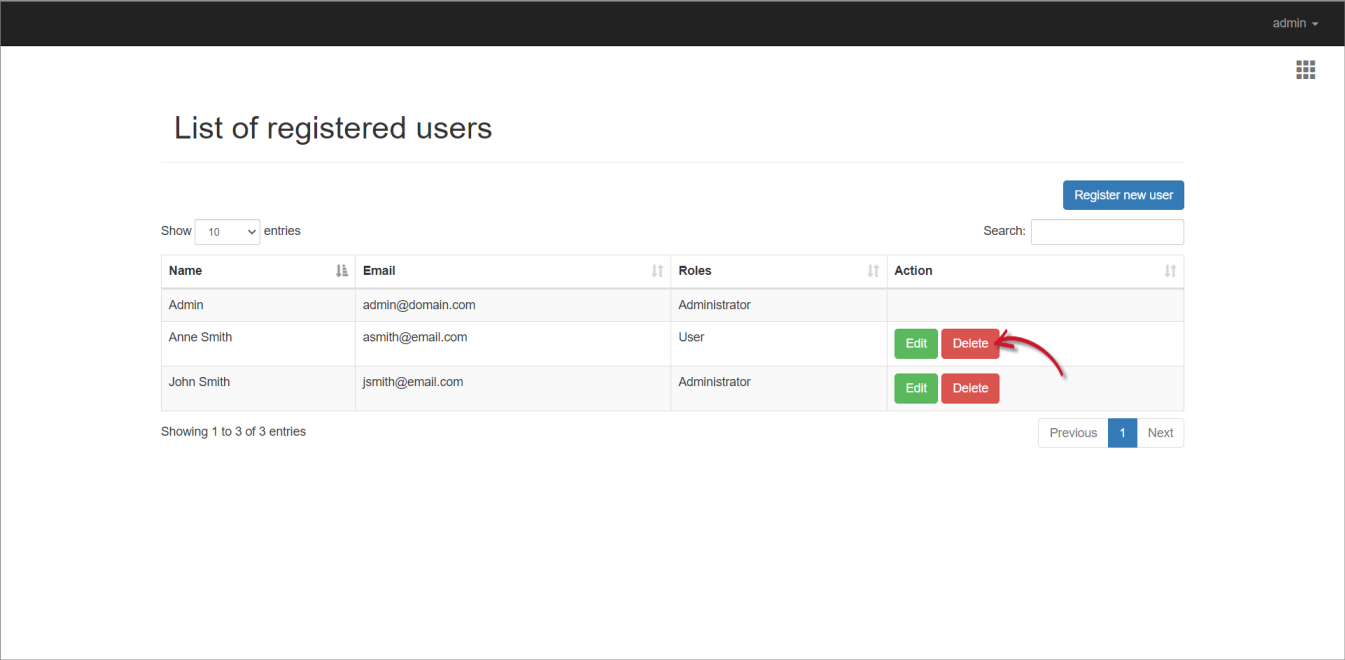
- Click Continue to proceed.
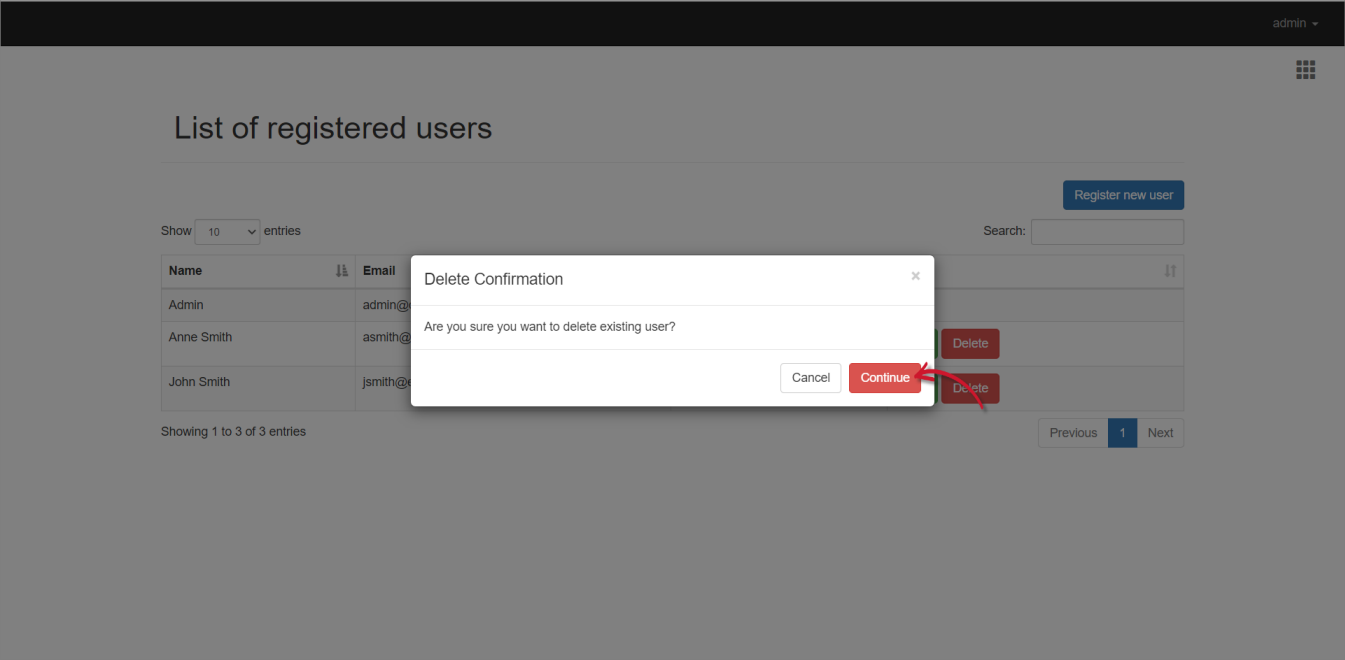
#
Managing Access Controls
Access controls let administrators decide on what users can do in CLIMS.
With access controls, you can grant permissions, limit available pages, and apply specific access filters. You can set access controls for the following entity:
- Users using their Active Directory (AD) username
- Users using their email address from Identity Server
- Active Directory (AD) Groups
- Roles from Identity Server
The default access control, Everyone, applies to all non-admin users.
Once an access control is created, it takes precedence over the default access control.
#
Understanding how CLIMS Access Controls work
The scenarios below discuss the behaviors and limitations of CLIMS' Access Control.
- If a user belongs to multiple AD groups with different access controls, the user inherits all permissions granted to those AD groups.
- An access control with empty permission and filters (basic and/or advanced) adopts the permission and filters of the default access control, Everyone.
- An entity can have multiple access controls.
An access control will not take effect if:
- The AD username or AD group is
added to the Administrator Group in Authentication.json . - The user has the Administrator role in the Identity Server.
Administrator permissions always take priority over other access levels.
#
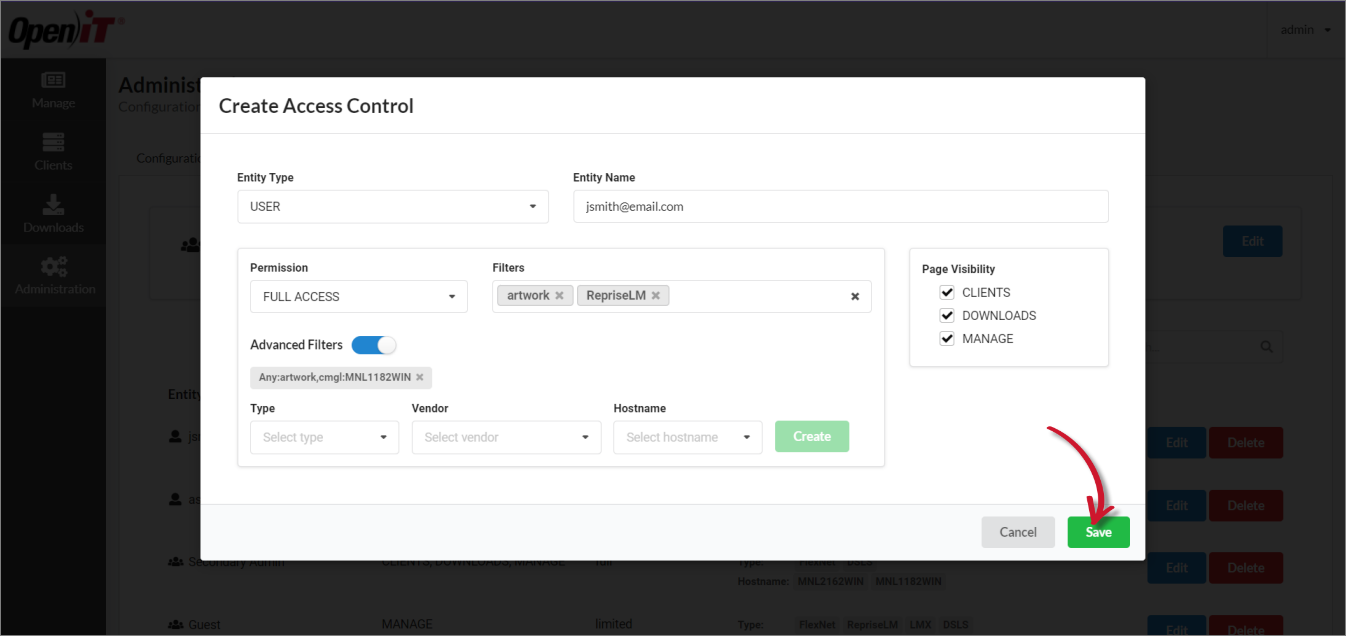
Create an Access Control
Log in using an Administrator account.
Go to Administration > Access Controls.
Click CREATE.
Choose the Entity Type. An access control can be for a specific user or role
Provide the Entity Name.
- If the Entity Type is User, type in the user's email address or AD account.
- If the Entity Type is Role, specify the role name or AD group.
For AD groups and usernames, follow the
domain\namesyntax.Choose a Permission.
Refer to the
- Add basic Filters.
- To grant full access to manage a specific license server: Select FULL ACCESS permission, then choose the specific license type.
- To grant full access to manage multiple license servers: Select FULL ACCESS permission, then choose the desired license types.
- To grant limited access to manage a specific license server: Select LIMITED ACCESS permission, then choose the specific license type.
- To grant full access to manage a specific vendor: Select FULL ACCESS permission, then choose the specific vendor daemon.
- To grant full access to manage multiple vendors: Select FULL ACCESS permission, then choose the desired vendor daemons.
- To grant full access to manage license servers in a specific machine: Select FULL ACCESS permission, then choose the specific machine hostname.
- To grant full access to manage license servers in multiple machines: Select FULL ACCESS permission, then choose the machine hostnames.
- To grant limited access to manage license servers in a specific machine: Select LIMITED ACCESS permission, then choose the specific machine hostname.
For complex filters that require relationship between multiple filter values, enable the Advanced Filters option.
Formulate the advance filter(s), then click Create.
- Under Page Visibility, select the pages that will be accessible to the access control.
- Click Save.
#
Edit an Access Control
Log in using an Administrator account.
Go to Administration > Access Controls.
Click the Edit button of the target access control.
Update as needed.
Click Save.
#
Delete an Access Control
Log in using an Administrator account.
Go to Administration > Access Controls.
Click the Delete button of the target access control.
- Click Yes to continue.
#
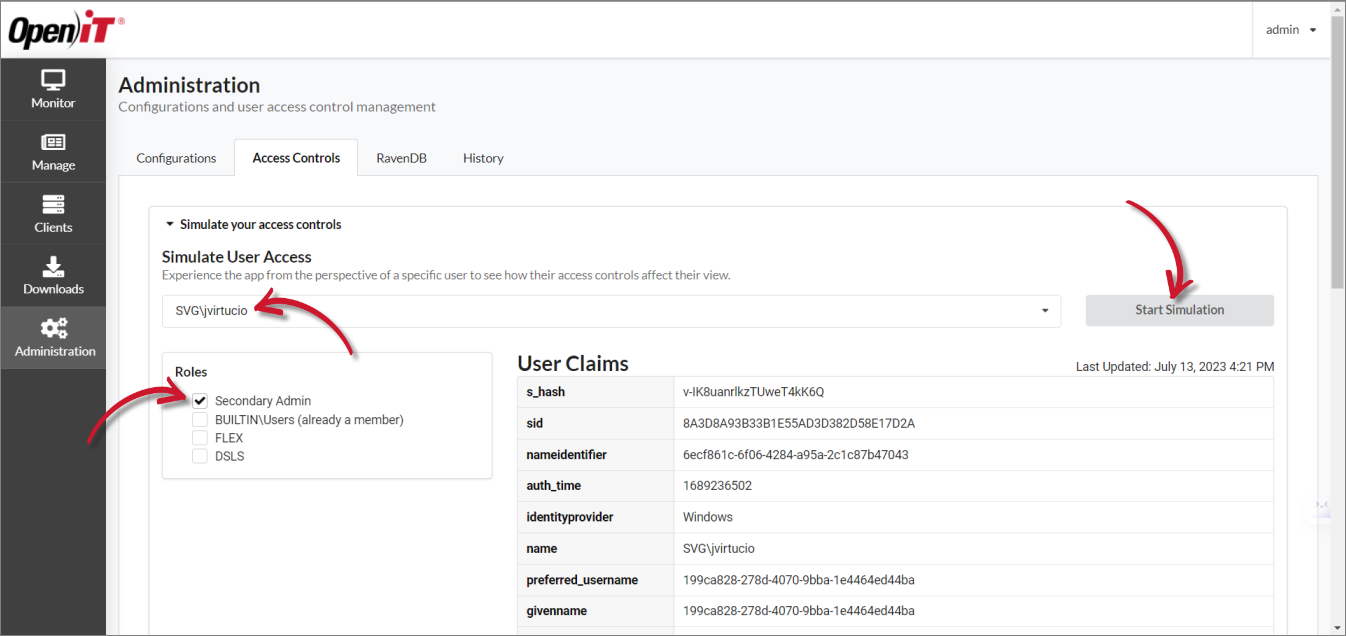
Simulating a User Access
Administrators can simulate user access to experience the perspective of a specific user and see how their access controls affect their view.
To start a simulation:
Log in using an Administrator account.
Go to Administration > Access Controls.
Click on Simulate your access controls.
Choose the user you want to simulate.
Select the role(s) you want to experience in the simulation.
Click Start Simulation.
- Click Confirm.
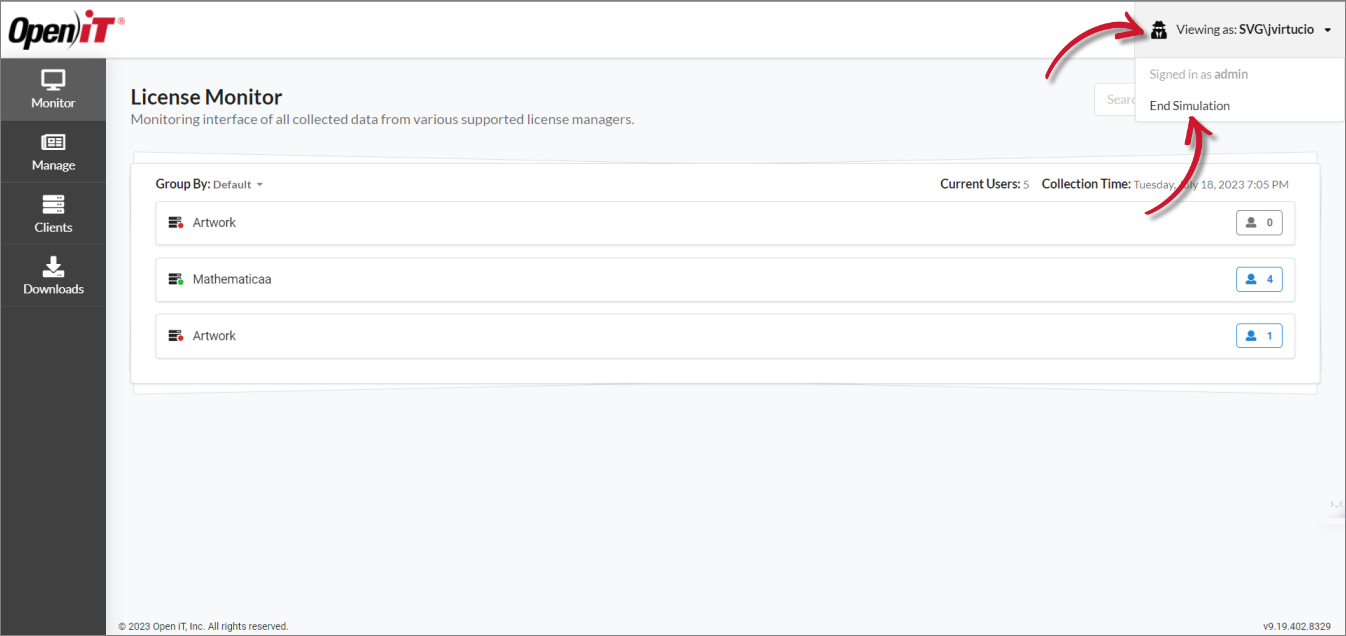
To end a simulation:
On the upper-right corner of the page, click on
Viewing as:<User>.Click End Simulation.